External Authentication
Enabling LDAP authentication in SAS Enterprise Session Monitor allows developers to view the log files and manage their own sessions in a authenticated, audited way. When enabled, users will be able to authenticate using their normal Active Directory or LDAP account to view the log files or kill sessions where the username of the authenticated user matches the username of the owner of the session.
LDAP integration for SAS Enterprise Session Monitor can be done through the User Interface from the Privileged Users tab of the Admin Settings section of the application. In the top left of the tab, click the "Configure LDAP" button.
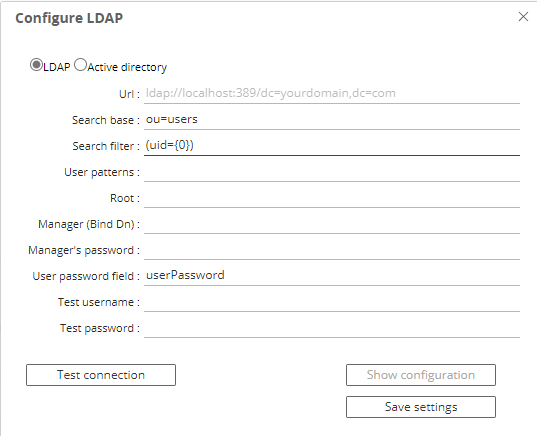
Alternatively, on your Enterprise Session Monitor Server machine, and depending on whether you are connecting to either Active Directory or another LDAP provider such as OpenLDAP, you can create a file called either ad.properties or ldap.properties in the following (relative) path of your SAS Enterprise Session Monitor server installation: esm-server/conf. The user interface method creates this file in the background.
After the initial configuration either the user interface or a text editor to the configuration file can be used to make changes. The Enterprise Session Monitor Server needs to be restarted in order for changes to be picked up.
Active Directory Properties¶
An ad.properties file could should contain, at a minimum, the properties marked as required below:
| Name | Value | Notes |
|---|---|---|
ad.url |
ldap://<host>:<port>/ |
Required The URL of the Active Directory server that you are connecting to. |
ad.domain |
boemska.local |
Required The name of the domain that you are connecting to. |
ad.searchFilter |
Optional An AD search filter is used to define criteria to provide more efficient and effective searches (MS docs) |
LDAP Properties¶
An ldap.properties file could should contain, at a minimum, the properties marked as required below:
| Name | Value | Notes |
|---|---|---|
ldap.url |
ldap://<host>:<port> |
Required The URL of the LDAP server that you are connecting to. |
ldap.userSearchBase |
ou=users |
Required Example: |
ldap.userSearchFilter |
(uid={0}) |
Required The {0} is important as this represent the value that is to be searched for. |
ldap.root |
/dc=company,dc.com |
Optional. The root can be specified using the /dc=company,dc.com on the connection string URL. |
ldap.userDn |
CN=ESM Binder,cn=Users,dc=boemska,dc=local |
Optional. If the LDAP server that you are connecting to doesn't accept anonymous binds then you must specify an account with which to perform the initial LDAP server bind. |
ldap.password |
Optional. This is the valid password that corresponds to the user that is specified in ldap.userDn. |
Created: April 24, 2023